How Security Service Edge (SSE) Is Deployed Within the SASE Architecture
Different architectural models of SASE allow for varying deployment and usage of SSE to support different use cases. As SASE provides different benefits and drawbacks, a hybrid SASE architecture provides the necessary balance between flexibility, security, and cost
Updated May 10, 2024

Cloud-delivered security services have been offered in the market and used by enterprises for many years. By coining the term SSE (Security Service Edge), Gartner created a clear definition and understanding of what such services should comprise as it unifies the various technologies into a comprehensive architecture. This is an important step as enterprises increasingly shift towards digital platforms and cloud-delivered applications that require the right balance between agility and security.
The Emergence of SSE
SSE could be defined as the security component of SASE (Secure Access Service Edge)—an architecture that unifies SD-WAN with important security functions. It's a cloud-delivered security system where everything resides in the cloud, including all traffic that must be routed through this cloud security service.
The emergence of Security Service Edge (SSE) has helped clarify the domain of cloud-delivered cybersecurity, driven by the evolving needs of modern enterprises for more integrated and flexible security solutions. In response to the demand for security services that cater to single-vendor environments as well as offering a broader choice and control over network architecture, Gartner coined the term SSE in 2021 to give a name to an existing technology.
SSE encompasses critical security functions, all delivered from the cloud to ensure comprehensive protection across the enterprise's digital assets. This model represents a shift towards a more cloud-centric security approach, where all traffic is routed through cloud-based security services. It offers enhanced capabilities while also introducing challenges in flexibility, choice in vendor selection, architectural design, and cost optimization.
Core Components of SSE
-
Zero Trust Network Access (ZTNA): Implements the principle of "never trust, always verify," granting access based on strict identity verification and least privilege, regardless of the user's location. - Secure Web Gateway (SWG): Provides safe access to the web by enforcing company policies, thus preventing exposure to threats and restricting access to malicious websites.
- Cloud Access Security Broker (CASB): Acts as a mediator between users and cloud services, enforcing security policies, and providing visibility into cloud application usage.
- Firewall as a Service (FWaaS): Offers next-generation firewall capabilities in the cloud, including intrusion prevention, application control, and advanced threat protection.
These components, when bundled together and delivered from the cloud within the SSE framework, create a robust security architecture that ensures comprehensive protection for cloud access, enhances visibility across all user activities, and maintains compliance with security policies.
Gartner's Models of SASE
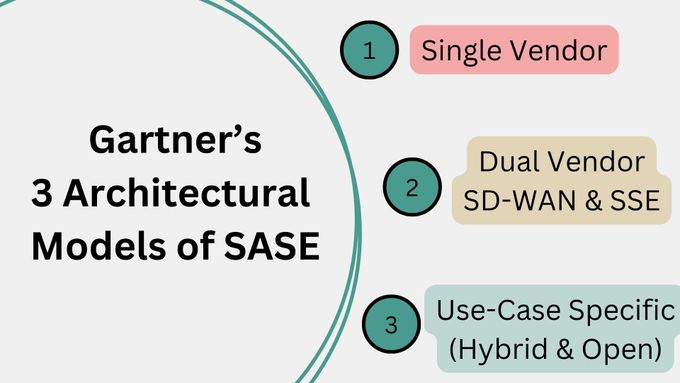
In April 2022, Gartner published a paper that describes the three architectural models of SASE. This came as a response to the market reality of various SASE deployments other than the original single vendor definition of SASE. In real life, enterprises have different requirements when it comes to cost, vendor selection (including a best-of-breed approach vs. a single vendor one), and different schedules for end of life of existing products already deployed in the enterprise network.
- Single Vendor SASE Model: This model represents a unified solution where SD-WAN and security components, including SSE functionalities, are provided by a single vendor. It's described as a siloed approach, potentially leading to vendor lock-in but offering a streamlined integration of networking and security.
- Dual Vendor Model: In this approach, an organization might opt for SD-WAN from one vendor (Vendor A) and SSE components from another (Vendor B). The network backbone on which data is transported typically comes from the SSE provider. This model seeks to balance integration with vendor diversification.
- Use-Case Specific Model (or Hybrid): This is a more flexible and open architecture that allows for greater choice in SASE vendor selection and network design. It's not strictly tied to single or dual vendor constraints, enabling organizations to tailor their SASE implementation more closely to specific needs, including the choice of routing policies and the integration of existing network assets.
As an approach, SSE enhances cloud-era enterprise security but faces several challenges:
- Difficulty managing complex security policies across varied cloud services and environments.
- The need to consume and configure the full SSE stack although not all components are always required by all enterprises. This could potentially overwhelm IT resources, increase cost, and reduce agility.
- Dependency on a single vendor for SSE can result in vendor lock-in, affecting flexibility and possibly raising long-term costs.
- Latency issues may also arise from routing all traffic through SSE platforms, impacting performance for organizations spread across multiple locations.
» Learn more about SD-WAN, SSE, & SASE
Solve SASE Challenges With a Hybrid SASE Architecture
To address the challenges posed by single-vendor and dual-vendor SASE models, the solution gravitates towards embracing a more open, flexible architecture.
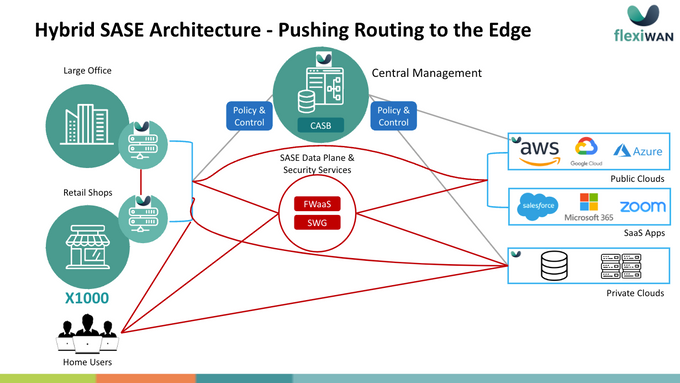
A hybrid SASE architecture combines the strengths of both models while mitigating their limitations. It allows for routing decisions to be pushed to the network edge, enabling organizations to tailor their security and connectivity strategies to their specific needs.
A hybrid approach not only provides the flexibility to use different vendors for SD-WAN and security services, thereby reducing the risk of vendor lock-in and fostering a competitive environment that can lead to cost savings and innovation. It also allows for more control over the routing policy as depicted in the image below.
The Hybrid-SASE architecture supports direct internet access for selected services and applications (policy configured by IT), optimizing performance and cost while reducing latency by allowing traffic to bypass the centralized security services when appropriate. It acknowledges the diversity of enterprise needs, offering a customizable approach that can adapt to various operational scenarios.
By incorporating the ability to configure specific routing policies and security measures at the edge, enterprises gain greater control over their network architecture, enhancing both security and efficiency. This solution underscores the importance of a strategic, adaptable approach to network and security planning, ensuring organizations can navigate the complexities of the digital landscape.