Understanding The Alphabet Soup of SD-WAN, SSE & SASE to Avoid the Premium Cost and Shackles of a Single Vendor Selection
Let the Olympics of enterprise networking and security begin!
Updated May 10, 2024.
Using Gartner’s terms for naming the 5 phases of the technology lifecycle to measure hype, the confusion around acronyms used in enterprise networking and security, and the marketing fads and disinformation around them are at the peak of inflated expectations.
This blog post demystifies the confusion around SD-WAN, SSE, and SASE, what they are, and the optional architectures for deploying them.
History
MPLS (Multiprotocol Label Switching) was invented back in the 90s and is still around today, but the WANs (Wide Area Networks) it serves and how applications are consumed has completely changed.
SD-WAN Is Born
The term SD-WAN (Software Defined WAN) came along around 2014, making use of several existing technologies and putting them under one umbrella. SD-WAN stems from several technology advancements and changes in the design of enterprise networks. The main factors that made it successful include:
- The shift of applications to the cloud and the need to deliver them securely and in a high-quality experience
- Increased processing power that made it possible to create application-aware software-based networking solutions
- The ability to utilize general-purpose broadband and wireless connections while optimizing the traffic flow over them
- The separation between the control and the data planes
- Central management
- The increased importance of security
SASE Is Coined and Hyped
A few key factors led to the coining of the term SASE (Secure Access Service Edge):
- Availability and popularity of security services in the cloud
- The advancement of Zero Trust, a concept that was developed long before this time and in 2010 used by Forrester Research as a model for stricter enterprise security
- The integration between networking (SD-WAN) and security – At first, mainly as an on-premise solution, either as one unified product or through the concept of VNFs and uCPE, and later, it shifted to integrations between SD-WAN products and cloud security services
- The increasing demand for the consumption of cloud applications, which required securing access to them and ensuring the quality of experience
- Companies that offered the single and monolithic option of the SASE architecture (prior to coining the term SASE) with strong financial backing and marketing capabilities that created the hype around the concept
These together, combined with the desire to innovate and differentiate from competing analyst firms, drove Gartner to coin the term SASE in 2019.
The hype around SASE quickly placed it at the peak of inflated expectations on the Gartner Hype Cycle for Enterprise Networking in 2020. The hype around SASE was so strong that one company came out with a marketing campaign that said, “SD-WAN is Dead, Long Live SASE” (you will not find it in their marketing messaging anymore).
The market reality proved to be different, enterprises and service providers were deploying a variety of architectures and variations of the theoretical SASE recommendation. Moreover, vendors offered a variety of combinations of the elements of SASE (more on what they are, below).
SSE Offers Less Monolithic One-Size-Fits-All Architectures
As the market voted with its feet and budget decisions for variations of SASE, in 2021, Gartner coined a new term, SSE (Security Service Edge), which, in essence, is a cloud-delivered security service offered as a unified platform. This move gave a name to the existing services offered by several security companies, such as Zscaler.
What Is SASE?
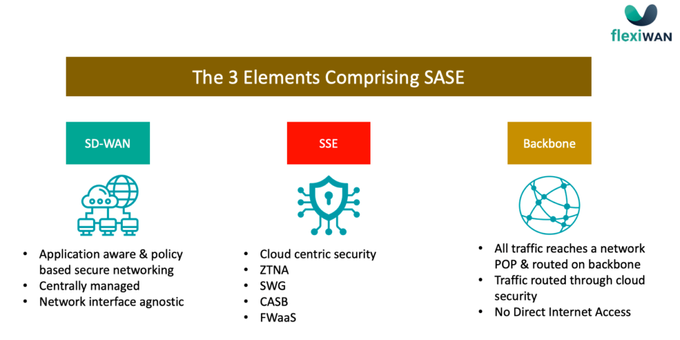
As mentioned above, SASE is Secure Access Service Edge. It is a single architecture that combines three main elements, as depicted in the illustration below.
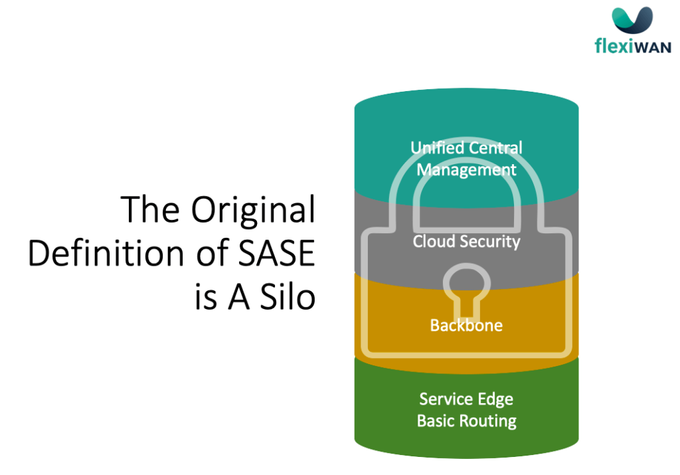
The initial definition of SASE by Gartner was a single vendor cloud-delivered network and security. It required the use of a backbone, provided by that same vendor (that, in practice, became a service provider), and dictated a routing policy that doesn’t allow Direct Internet Access (DIA) from branch locations of users’ devices—but rather, routes all traffic from the user to the first POP (Point of Presence) of the vendor, from there, over the backbone, through the cloud security and to the POP from which it exits to the internet.
Later in 2022, Gartner defined 3 architectures:
- A single-vendor SASE architecture (what we explained above)
- An integrated dual-vendor architecture separating the SD-WAN and SSE vendors and having the backbone come from the SSE vendor with tight integration with the SD-WAN vendor
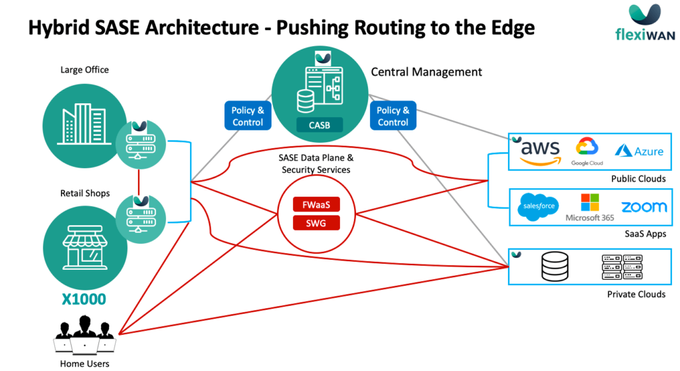
- A Use-Case Specific-Solutions, No SASE – I would include in this any variation of the SASE architecture that would adopt some of the SASE concepts but would allow for more options to support the enterprise or service provider business needs. I name it “Hybrid SASE”
Hybrid SASE
Given the strict and monolithic routing architecture defined in SASE, a Zoom call or consumption of a YouTube video clip will be mandatorily routed over the backbone of the SASE vendor (remember, the vendor now is practically a service provider) and through its security.
This introduces business challenges due to the increased cost of network operations, and user experience challenges that vary based on the quality and geolocation of the backbone of each vendor.
The single vendor architecture reduces the competitiveness in the market as fewer companies can offer it and fewer enterprises can afford it:
- Offered by: large vendors or service providers that can financially support a high-quality and globally distributed backbone. Smaller vendors and service providers need to partner with other companies in order to offer the full suite
- Offered to: The cost of the backbone and the fact that all traffic MUST be routed over it and through the cloud security, comes with a high cost that is rolled over to the end-user. This, in turn, causes SASE to be consumed by large enterprises that can bear the cost. There are other cases in which SASE is offered at a more competitive price that results either in very low margins or a non-sustainable, non-profitable price
Overcoming these challenges and optimizing the deployment of SASE to better support the dissimilar requirements of enterprises and service providers requires pushing routing decisions to the edge.
The illustration above is an example of such hybrid architecture where part of the traffic is routed through cloud security while other traffic is routed directly to the internet.
The policy defining which traffic should run over the backbone and through the cloud security and which can be sent directly to the internet should be implemented at the edge (branch, user device).
The system itself is still centrally managed. All policies, security configuration, software updates, and the general management of the system are configured in one place (UI) and pushed to all of the edge devices.
Since DIA is allowed if defined by IT in the policy, local security should be deployed. Depending on the policy itself and the type of traffic designated to DIA, the security strategy should be decided. In many cases, simple access control at the edge would do the job.
In Conclusion
SASE is never a one-size-fits-all.
In order for the SASE concept to be successful and dominant among all sizes of enterprises and service providers, it is required to allow for disaggregation of HW and SW and of the SW stack itself so different elements could come from different vendors.
The application concept that flexiWAN, together with the unlocking of routing policy defined in the theoretical SASE recommendation, brings the Hybrid SASE to the forefront.